Confidential Computing

Overview
Introduction
In the rapidly changing cloud landscape, security and privacy are key concerns for businesses and individuals alike. Confidential Compute turns out to be a possible solution, ensuring sensitive data remains private and secure even in shared computing environments. In this blog post, I want to explain the concept of Confidential Compute in general and explore the specifics of how Azure has implemented confidential compute and how this can help with cloud sovereignty.
Understanding Confidential Compute
NIST definition for confidential compute: Hardware-enabled features that isolate and process encrypted data in memory so that the data is at less risk of exposure and compromise from concurrent workloads or the underlying system and platform. Source: NISTIR 8320
Confidential computing is a set of technologies that protect data in use, even when it is being processed. In traditional computing, data is typically encrypted when it is at rest (stored on disk) and in transit (moving across a network), but it is often decrypted and exposed in memory when it is being processed by the CPU. Confidential computing aims to address this vulnerability by providing a secure enclave for sensitive data during processing. This is achieved through the use of Trusted Execution Environments (TEEs), which are isolated areas of a computer's memory that are designed to protect against unauthorized access. These enclaves allow for the execution of code and processing of data in a secure environment, shielding it from the rest of the system and even from privileged software.
AMD Secure Encrypted Virtualization (SEV) is a technology developed by AMD that provides hardware-based memory encryption for virtual machines (VMs). SEV uses a unique key to encrypt the memory of each VM, which is managed by the AMD Secure Processor. This helps to isolate guests and the hypervisor from one another, thereby providing an additional layer of security. SEV requires enablement in the guest operating system and hypervisor.
Intel SGX (Software Guard Extensions) and AMD SEV (Secure Encrypted Virtualization) are examples of hardware-based technologies that enable confidential computing. These technologies provide a secure execution environment for applications by creating isolated enclaves within the CPU. Additionally, there are software-based approaches, such as Microsoft's Azure Confidential Computing and Open Enclave SDK, which provide a platform-independent way to build confidential computing solutions.
Intel Software Guard Extensions (SGX) is a set of instruction codes implementing trusted execution environment that are built into some Intel central processing units (CPUs). They allow user-level and operating system code to define protected private regions of memory, called enclaves. SGX is designed to be useful for implementing secure remote computation, secure web browsing, and digital rights management (DRM). Other applications include concealment of proprietary algorithms and of encryption keys. SGX involves encryption by the CPU of a portion of memory (the enclave). Data and code originating in the enclave are decrypted on the fly within the CPU, protecting them from being examined or read by other code, including code running at higher privilege levels such the operating system and any underlying hypervisors. While this can mitigate many kinds of attacks, it does not protect against side-channel attacks. SGX was first introduced in 2015 with the sixth generation Intel Core microprocessors based on the Skylake microarchitecture. Support for SGX in the CPU is indicated in CPUID “Structured Extended feature Leaf”, EBX bit 02, but its availability to applications requires BIOS / UEFI support and opt-in enabling which is not reflected in CPUID bits. This complicates the feature detection logic for applications. Emulation of SGX was added to an experimental version of the QEMU system emulator in 2014. In 2021, Intel deprecated SGX from the 11th and 12th generation Intel Core Processors, but development continues on Intel Xeon for cloud and enterprise use. Source: Wikipedia
Confidential computing offers several benefits for safer handling of sensitive data while in use
- Added security in shared, untrusted, or unfamiliar environments: Confidential computing techniques and technologies give your sensitive data more safeguards, regardless of the computing environment.
- Secure data input and output: Confidential computing ensures that data is encrypted in memory and processed only after verifying the cloud environment as a trusted execution environment, preventing data access by cloud providers, malicious administrators, and authorized software.
- Equal focus on security and cloud computing capabilities: Confidential computing enables entirely new security standards that prevent breaches, malware, malicious insiders, and keep hackers out.
- Remote quality assurance capabilities: Confidential computing allows for remote quality assurance capabilities, which can help organizations save time and money.
- Easier detection and prevention of unauthorized access: Confidential computing provides a secure environment for processing data in the cloud, which makes it easier to detect and prevent unauthorized access.
- Compatibility with data privacy and compliance requirements: Confidential computing is compatible with data privacy and compliance requirements, such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA).
- Protection for data in use: Confidential computing protects data in use by performing computation in a hardware-based, attested Trusted Execution Environment (TEE), which prevents unauthorized access or modification of applications and data during computation.
Azure and Confidential Compute
Azure Confidential Computing is a Microsoft Azure service that provides a secure environment for processing sensitive data. It is designed to protect data in use by performing computations in a hardware-based Trusted Execution Environment (TEE). Confidential computing is an industry term defined by the Confidential Computing Consortium (CCC), a foundation dedicated to defining and accelerating the adoption of confidential computing. The CCC defines confidential computing as the protection of data in use by performing computations in a hardware-based, attested Trusted Execution Environment (TEE). These TEEs prevent unauthorized access or modification of applications and data during computation, thereby always protecting data . Azure Confidential Computing provides a range of features that enable customers to configure and protect their data and resources in ways that help them comply with their specific regulatory, security, and sovereignty requirements . Some of the key features include:
- Confidential secrets management
- Confidential analytics services
- Control over access to customer workloads
- Protection of proprietary business logic, analytics functions, machine learning algorithms, or entire applications
- Elimination of the single largest barrier of encryption - encryption while in use
- Protection of sensitive or highly regulated data sets and application workloads in a secure public cloud platform
Benefits of Azure's Confidential Compute:
Data Confidentiality Protects sensitive data throughout its lifecycle, from processing to storage. Mitigates the risk of data breaches and unauthorized access.
Regulatory Compliance Helps organizations comply with strict data protection regulations by providing a robust security framework.
Versatility Supports a wide range of workloads, from traditional applications to modern containerized environments.
Developer Friendly Azure Confidential Compute integrates seamlessly with popular development tools and frameworks, making it accessible for developers.
Azure Confidential Computing can be used on-premises or in a hybrid cloud environment by using Azure Stack HCI, which is a hyper-converged infrastructure (HCI) cluster solution that runs virtualized Windows and Linux workloads in a hybrid on-premises environment . Azure Stack HCI provides a consistent Azure experience on-premises, enabling customers to run Azure services on-premises and in the cloud. In addition, Azure Arc enables customers to manage servers, Kubernetes clusters, and applications across on-premises, multi-cloud, and edge environments. Azure Arc provides a single control plane for managing resources across environments, enabling customers to use Azure services anywhere.
Current Confidential Compute features (General available)
Azure Confidential VMs Azure Confidential VMs provide a secure foundation for sensitive workloads. By leveraging Intel SGX (Software Guard Extensions) technology, these virtual machines create a confidential enclave where data can be processed in a secure and isolated environment. This ensures that even the cloud service provider cannot access the data during processing.
Azure Kubernetes Service (AKS) with Confidential Nodes For containerized workloads, Azure introduces Confidential Nodes in AKS. This allows organizations to run confidential workloads in Kubernetes clusters, maintaining the same level of security as Confidential VMs. This is particularly valuable for applications that rely on container orchestration.
Azure Attestation Azure Attestation is a service that remotely validates the trustworthiness of a confidential enclave. It enables developers to ensure that their code is running within a secure environment, protecting against potential threats. This attestation capability enhances the overall security posture of applications leveraging Confidential Compute.
Azure IoT Edge with Confidential Compute Extending the benefits of Confidential Compute to the edge, Azure IoT Edge enables secure and private processing of data on IoT devices. This is crucial for scenarios where real-time processing is required without compromising on security.
Cloud for Sovereignty
The term cloud sovereignty refers to the concept of ensuring that data and operations in the cloud are subject to the laws and regulations of the country or region in which they are located. It involves addressing concerns related to data governance, legal jurisdiction, and compliance with local regulations when using cloud computing services.
Cloud sovereignty is particularly relevant when organizations or governments want to maintain control over their data and ensure that it is subject to the legal frameworks of their own jurisdiction. Some countries or industries have specific regulations regarding data storage, processing, and access, and cloud sovereignty aims to address these requirements.
Aspects of cloud sovereignty are:
Data Location Organizations may have legal or regulatory obligations to store certain types of data within specific geographic boundaries. Cloud sovereignty involves ensuring that data is stored in data centers located within the jurisdiction specified by applicable laws.
Data Access and Control Organizations may want to retain control over who can access their data and under what circumstances. This involves understanding and negotiating the terms of service with cloud providers to ensure compliance with legal requirements related to data access and control.
Legal and Regulatory Compliance Cloud sovereignty addresses the need to comply with local laws and regulations, including data protection laws, privacy regulations, and other legal requirements that may vary from one jurisdiction to another.
Security and Compliance Standards Ensuring that the cloud infrastructure and services adhere to security and compliance standards that are recognized or mandated by the jurisdiction is a crucial aspect of cloud sovereignty.
Risk Management Organizations need to assess and manage the risks associated with using cloud services, taking into account the legal, regulatory, and geopolitical considerations that may impact the sovereignty of their data.
Microsoft Cloud for Sovereignty
Microsoft Cloud for Sovereignty is a cloud solution that enables, for instance public sector customers to build and digitally transform workloads in the Microsoft Cloud while supporting a variety of compliance, security, and policy requirements. It features platform capabilities that unlock greater resiliency, agility, and security while offering greater control over data and increased transparency to the operational and governance processes of the cloud. The solution is designed to help mitigate sovereignty risks by providing a resilient, scalable, and agile platform for (public sector) customers to deploy their sovereign workloads by combining the power of the global Azure platform with several sovereignty capabilities. These capabilities include data residency, confidential computing, document classification, and hybrid deployments. The solution also provides customers with access to local partners who have technical and industry experience to help them plan, incorporate, govern, and operate their cloud environments
Sovereign Landing Zone
As part of the Cloud for Sovereignty, Microsoft offers the Sovereign Landing Zone (SLZ). This landing zone is based on the Azure Landing Zone. The difference in the architecture is that you get next to corp and online landingzones also a confidential corp and confidential online landing zone. Using policy as code, you set specific security and privacy related policies on the confidential landing zones.
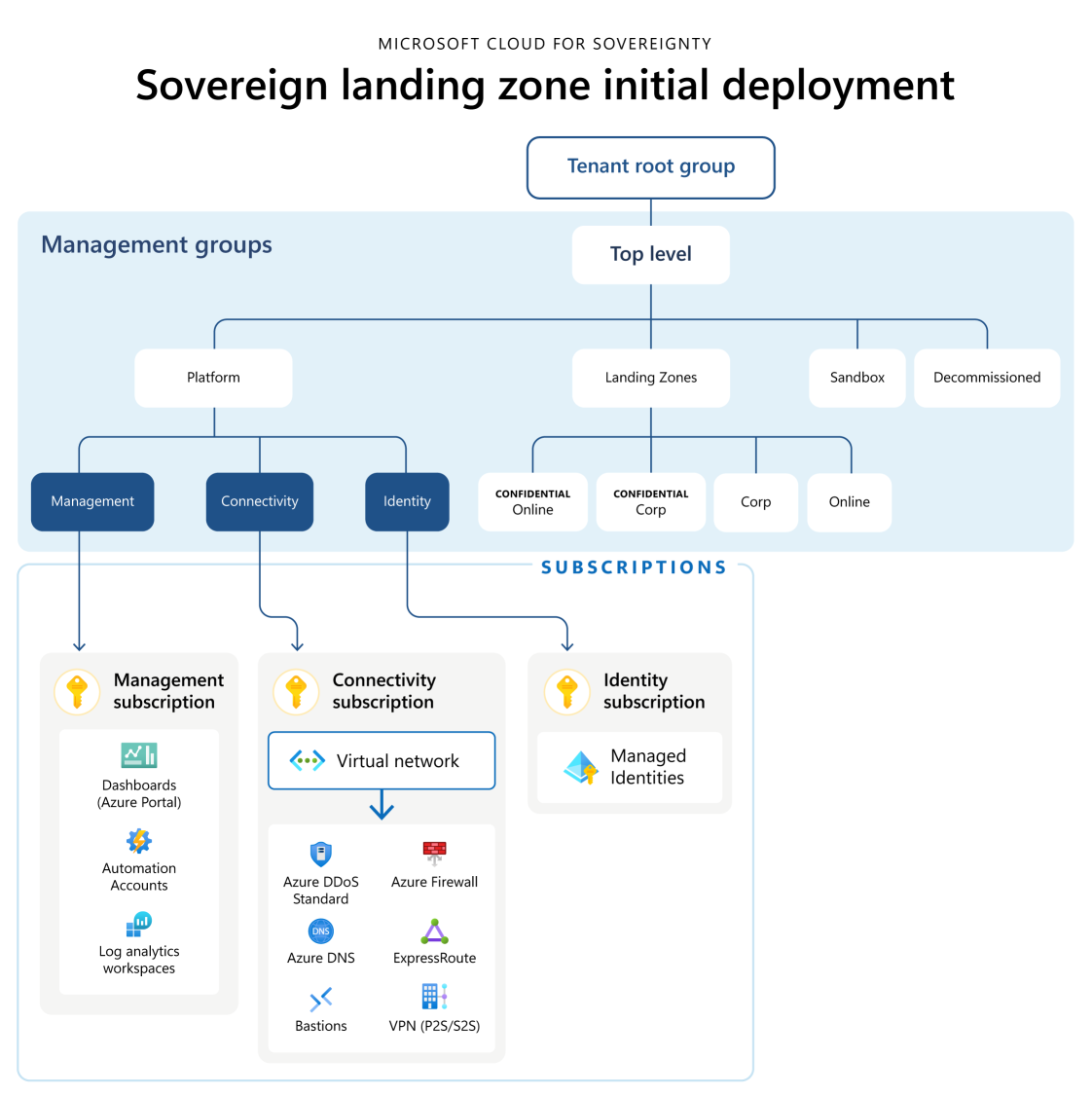
Another difference between 'normal' corp and online landingzone and the confidential corp and online landingzone is that the latter will only allow services based on Azure confidential computing (ACC). ACC reduces the need for trust across various aspects of the compute cloud infrastructure. Azure confidential computing minimizes trust in both the system processes, such as the host OS kernel and the hypervisor, and human operators that include the VM admin and the host administrator. With the guardrails and compliance enforcement of Microsoft Cloud for Sovereignty, ACC provides enhanced protection of sovereign, sensitive or highly regulated data and workloads within the scalability, flexibility, availability, and services of the Azure platform. The SLZ is currently in preview. More information regarding the SLZ can be found here. For instructions how to configure and or deploy the Sovereign Landing Zone, visit Github.
New Azure confidential compute features in Q4
In Q4 of 2023, Microsoft announced during Microsoft several new features in the confidential compute domain. Most of them are still in preview.
Microsoft Azure Managed Confidential Consortium Framework, now in preview, is a new Azure service that will offer execution of the Microsoft Confidential Consortium Framework (CCF) open-source SDKs as a managed service, eliminating the need for developers to stand up their own infrastructure to support a CCF API endpoint. Developers will be able to more easily build and manage confidential multi-party applications with decentralized trust on a secured and governed network of trusted execution environments. For more information read this blog
The confidential virtual machine (VM) option for Azure Databricks is now generally available. Customers seeking to better ensure privacy of personally identifiable information (PII) or other sensitive data while analyzing that data in Azure Databricks can now do so by specifying AMD-based confidential VMs when creating an Azure Databricks cluster. Running a customer’s Azure Databricks cluster on Azure confidential VMs enables Azure Databricks customers to confidently analyze their sensitive data in Azure. For more information read this blog
The DCesv5-series and ECesv5-series confidential virtual machines (VMs) are now in preview. Featuring 4th Gen Intel® Xeon® Scalable processors, these VMs are backed by an all-new hardware-based trusted execution environment called Intel® Trust Domain Extensions (TDX). Organizations will be able to use these VMs to seamlessly bring confidential workloads to the cloud without any code changes to their applications. For more information read this blog
New features and services for Azure confidential virtual machines (VMs) include Red Hat Enterprise Linux (RHEL) 9.3 support, Disk Integrity Tool, temporary disk encryption, new region support and trusted launch as default in PowerShell for all Azure Gen 2 VMs. RHEL 9.3 support for AMD SEV-SNP confidential VMs will allow Azure customers to specify the RHEL 9.3 image as the guest operating system (OS) for AMD-based confidential VMs. This will ensure any sensitive data processed by their RHEL guest OS is protected in use, in memory. Azure AMD-based confidential VMs provide a strong, hardware-enforced boundary that hardens the protection of the guest OS against host operator access and other Azure tenants. These VMs are designed to help ensure that data in use, in memory, is protected from unauthorized users using encryption keys generated by the underlying chipset and inaccessible to Azure operators. RHEL 9.3 support for AMD SEV-SNP confidential VMs is in preview.
Disk Integrity Tool for Intel TDX confidential VMs will allow customers to measure and attest to a disk in their confidential VM. The tooling comes as an Azure CLI extension that a user can install in their own trusted environment to run a few simple commands to protect the disk. When such integrity protected disks are used for confidential VM deployments, after the VM boots, users will be able to cryptographically attest that OS disk’s root/system partition contents are secure and as expected before processing any confidential workloads. Disk Integrity Tool for AMD SEV-SNP confidential VMs is in preview.
Temporary disk encryption for AMD SEV-SNP confidential VMs will allow Azure customers to encrypt the temporary disk attached to their AMD-based confidential VMs using customer-managed keys. This ensures any sensitive data on those disks is protected at rest. Temporary disk encryption for AMD SEV-SNP confidential VMs is in preview.
New region support for AMD SEV-SNP confidential VMs is now generally available in the following new regions: Southeast Asia, Central India, East Asia, Italy North, Switzerland North, Japan East, Germany West Central and UAE North.
Trusted launch as default in PowerShell for all Azure Gen 2 VMs, now generally available, hardens Azure Virtual Machines with security features that allow administrators to deploy virtual machines with verified and signed bootloaders, OS kernels and a boot policy. This is accomplished via such trusted launch features as secure boot, vTPM and boot integrity monitoring that protect against boot kits, rootkits and kernel-level malware. For more information read this blog
The NCCv5 series confidential virtual machines with NVIDIA H100 Tensor Core GPUs, in preview, will be the first and only cloud offering of its kind that will allow AI developers to deploy their GPU-powered applications confidentially. This will ensure data in both CPU and GPU memory is always encrypted by using keys generated by hardware and is protected from unauthorized alteration. Data scientists needing to train their models and gain insights from multiple third-party data sources will be able do so while ensuring personal data and AI models are kept private and provide evidence of their confidentiality through attestation reports. For more information read this blog
Confidential containers on Azure Kubernetes Service (AKS) is the first cloud service offering pod-level isolation and memory encryption in a managed Kubernetes service based on the open-source Kata containers project and powered by AMD SEV-SNP. Organizations will be able to migrate their most sensitive container workloads to the cloud without any code changes, while protecting their data in memory from external and internal threats. Confidential containers on AKS is now in preview. For more information read this blog
Conclusion
In conclusion, confidential computing is a technology that helps in providing a secure environment for processing data in the cloud and is here to stay. The technology used is relatively new, so I think there will be a lot of innovation in the near future. Microsoft offers with Azure Confidential Computing in combination with Cloud for Sovereignty a set of services which can support various use cases for securing data in use in different industries, such as government, financial services, and healthcare. If we look at the announcements at Ignite around confidential compute that Microsoft will not stop here but continue to expand on the confidential compute offerings. I think that in the near future, confidential compute will not be limited to the above mentioned use cases but will become the new normal same as disk encryption.